
TrustedInstaller is a built-in service account in the Windows operating system with the highest permissions. Introduced in Windows Vista, it is the Windows Module Installer service, which is part of Windows Resource Protection.
Thus, TrustedInstaller is responsible for managing system files, installing and uninstalling applications, and performing critical system updates. This ensures that important system files are not tampered with or modified by unauthorized users. This is accomplished by assigning ownership of system files to the TrustedInstaller account, which means that even an administrator cannot make changes to these files without first taking ownership of them.
Protecting these key resources is important to overall system stability, and, as such, they can only be modified by the Windows Module Installer service (TrustedInstaller.exe). If someone with administrative rights attempts to modify or replace a file that is protected by WRP, they will be presented with the message “Access Denied”.
However, if we look in the Local Users and Groups application you won’t find a TI user or group. This is because TrustedInstaller is a Service Account, meaning the service must be running when files owned by it are modified, and only the TrustedInstaller.exe can modify them.
We can use the Get-Acl cmdlet to read the security descriptor from a file and we can list the details.
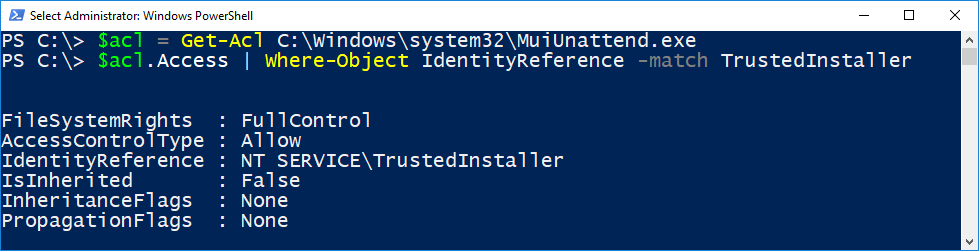
The IdentityReference member shows that we have got the TI group, and it’s prefixed with the domain “NT SERVICE”. Therefore, this is a Windows Service SID. This is a feature added since Vista to allow each running service to have groups which they can use for access checks, without the overhead of adding individual real groups to the local system.
Windows makes sure that it does not allow TrustedInstaller to be directly invoked. This prevents it from becoming the next generation of “Run as Administrator” bad advice.
But in case we have got ourselves into a situation which demands the modification of certain files and/or resources that is owned by TrustedInstaller, we can use the following method for gaining access to those resources.
• Download and Launch AdvancedRun from https://www.nirsoft.net/utils/advanced_run.html
• In the section “Program to Run:” browse and select the program. (Example: C:\Windows\System32\cmd.exe)
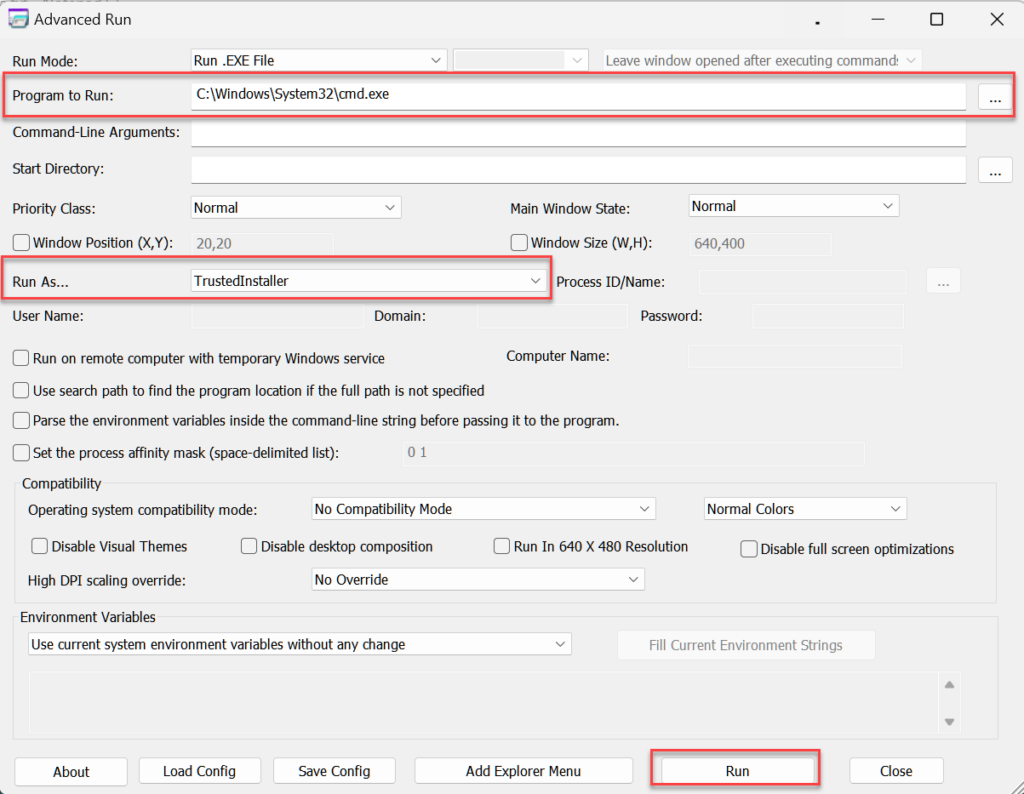
• In the section “Run As…”, select “TrustedInstaller”
• Click “Run”
The selected program will launch with the privileges of TrustedInstaller account.
Done.




