Unauthorized entry to the office premises is not the only major threat in the current day. Offices are prone to vandalism, theft, commercial espionage, terrorism and fraud. Though the regular practice of issuing identification badges to every visitor to the building is followed, how efficient is it?
Types of security systems for access control
Right now, the most common access control is by manual verification. Usually, a guard at the security post near the entrance manually verifies the ID. Even when there are further layers of security, some establishments, like government research labs or R&D facilities and similar areas where high security is needed, the first layer is usually manual verification. This, of course, has its drawbacks, the major one being the human resources required. Even in the presence of armed guards, manual verification is not completely secure. For one, the guards can’t be expected to remember everyone’s faces and ID cards are required. But the ID cards can easily be faked by an intruder.
Fingerprints, RFID, and barcode scanners are some of the most common access control technology that is adopted worldwide. While ID cards could be lost or stolen, fingerprints are much more secure. Fingerprint scanners are harder to fool, but not impossible.
A basic idea while designing any security system is that what is being guarded should be less valuable than the resources required to crack the security system. For example, if precious jewelry is being stored in a safe, the tools, the equipment, and the skills needed to crack open the safe must be more expensive than the value of the jewelry. If information is being stored, time also becomes a factor. This is a key factor when designing encrypted communication systems; if the usefulness of encrypted information becomes void by the time the message is decrypted, there is no point in attempting to decrypt it. There is no need for a steel vault worth millions to keep your bank account details secure if your bank balance is $10.
So, for most cases, a fingerprint scanner is more than enough for providing secure access. But in other applications where higher levels of security is required, a PIN or an alphanumeric password can be used, such as in the case of a bank vault. This brings us to another factor while designing security systems – convenience. While a PIN or a password is highly secure(of course it depends on the person using it and the password they’re choosing), it is not very convenient to enter a long password every time you need to access something. And password storage can also become cumbersome.
The advent of facial recognition.
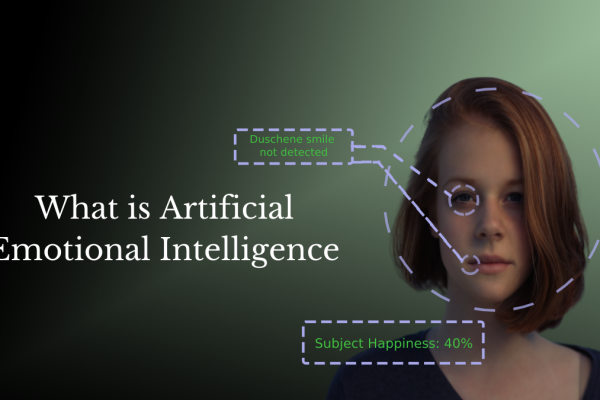
Facial recognition technology solutions provide a much more effective and reliable process of tracking visitors and developing a security check. This AI-powered automatic system captures the facial features of a person, adding an extra layer of security to the premises and provides secure access. So, how does this work?
A series of mounted cameras would capture the image of an individual entering the premises. The images captured from various angles are processed by the computer and are securely stored in a database. The data is synced with other information which would help in the identification of the individual in the visitor management system. A numerical code is often used to capture and identify the different facial features of humans, which includes the jawline, cheekbone, nose, forehead, mouth, and shape of the face. This process helps in concentrating on certain features and differentiating a person from others.
A well designed facial recognition system can overcome many of the difficulties mentioned above – “well designed” is the keyword. Facial recognition systems are fast, secure, and are difficult to fool. Of course, as I mentioned above, they have to be designed to be secure. News about facial recognition systems is usually about them being fooled by a picture or the system not recognizing the person under dim light.
Facial recognition systems are being used commonly in today’s smartphones. With the introduction of Face ID in the iPhone X, smartphone manufacturers have rushed to implement facial recognition systems in their phones. While Face ID relies on a 3D model of the face built using infrared sensors on the iPhone, most of the other systems seem to be relying on just the front camera. Even though this makes the system less secure, the system seems sufficient for the average person. The rush to make phones completely bezel-less has also led to wider adoption of facial recognition systems. They’re also being used in airports to provide a seamless experience to travelers.
Facial identification scanners are ahead of the conventional fingerprint or retina scanners. The facial recognition scanners offer seamless verification and are less intrusive. The facial recognition technology provides a much safer, more electronically prudent, reliable method of tracking office visitors, making the system efficient. The question is how we can make the best use of this technology.
Advantages over existing systems
- Convenient
- Difficult to fool
- Continuous monitoring of visitors
Convenience is one of the main reasons for the rapid adoption of facial recognition systems in today’s smartphones. Even though I see no reason why anyone would opt for a less than perfect facial recognition system over a simple and quick fingerprint scanner, I can totally picture people being lazy to press a finger on their phone. But unlike on a phone, while entering a building or an office a system that automatically authenticates entry using your face instead of having to press your fingerprint or show your badge can be very convenient.
The biggest advantage of the facial recognition system is security. The traditional access cards or fingerprint scanners can be easily manipulated. And here is where the facial recognition technology is effective. Face matching allows the system to adopt a more reliable approach in granting access and permission to an individual, making the system more robust and granting ease to the administration. Access control to your office is now easy. While a person leaves their fingerprint wherever they touch allowing anyone to copy and recreate it, a face is much harder to fake.
Another advantage is that, while conventional access control systems are usually one-time verification, a facial recognition system is capable of tracking a visitor the entire they’re inside the premises. Tracking the visitor in a building can be challenging, even in an office with small premises. A visitor can get lost while in a big establishment, a case where face recognition could track and help him/her. The facial recognition system could differentiate between an employee and a visitor, adding an extra layer of security. The system could also help in controlling unauthorized access. Visitor control is now easy.
Once a person is blacklisted by an organization, it’s easier for them to track the movements once the individual enters the premises and observe if any offending activities are taking place. The security quotient just got upped.
The advent of facial recognition technology has made way for complete automation in making a reliable security system. The system cuts down human intervention to a great extent for every step of identification. When a visitor visits again, the system can recognize the person and give him/her the necessary access. The system can identify the employees while negating the probability of any malpractices.
In recent news, Dubai police were able to nab 319 crime suspects with the help of 5000 AI-powered cameras installed in various parts of the city. The government has decided to use this technology to the maximum to realize the dream of “Zero Crime” city. The Kolkata police have installed over 3000 AI cameras in the city to armor the city against crime. AI cameras play a major role in keeping the premises, be it office space or cities, safe and crime-free.
Of course, as with any biometric system, there is an inherent security risk. The system is safe only as long as it is difficult to fake it. A system that uses biometric authentication is like a lock whose keys are thrown everywhere you go. Another concern is with regards to privacy. With government agencies getting facial recognition systems, the paranoia of being constantly monitored is becoming real every day. Implementation of facial recognition system
Whether your company is big or small, it’s ideal to apply a facial recognized authentication system, upping your security factor. We at Nuventure, put our skills and 10 years of experience into building reliable and efficient Artificial Intelligence (AI) based face recognition system for the industry. Let’s embrace the future.