What is a Supply Chain Attack?
A supply chain attack is a type of cyber attack where a hacker targets a third-party vendor or supplier in order to gain access to a larger organization’s network. Rather than attempting to penetrate a company’s defenses directly, hackers instead focus on identifying a vulnerable point in the supply chain. Basically it exploite trust realation between supplier and consumer.
This could be anything from a hardware component to a software application or service.
Once a vulnerable third-party is identified, the hacker will exploit it in order to gain access to the target organization’s network or data. This could involve installing malware or other malicious code onto a system, stealing login credentials, or using other social engineering tactics to trick employees into granting access.
In recent years, supply chain attacks have become an increasingly prevalent threat in the world of cybersecurity.
The blog explores what supply chain attacks are, why they are a significant threat, and examines some high-profile examples from the past five years.
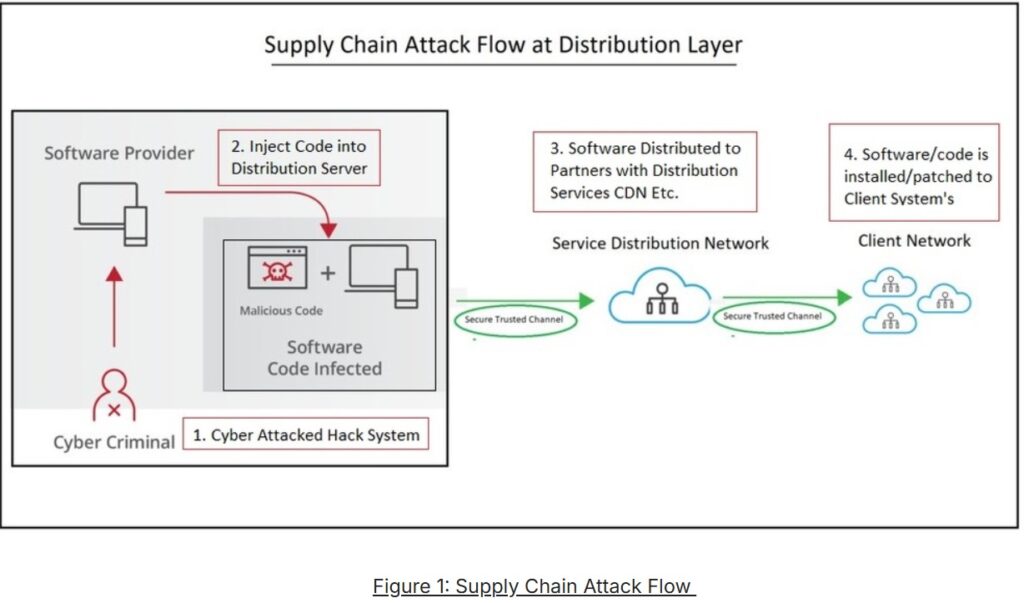
Examples of Supply Chain Attacks in the Past Five Years:
CCleaner (2017) – In 2017, hackers compromised the software update mechanism of the popular system cleaning tool CCleaner. This allowed them to install malware onto millions of computers around the world. While the attack was discovered before any major damage was done, it highlighted the vulnerability of software supply chains.
NotPetya (2017) – NotPetya was a ransomware attack that originated from a Ukrainian accounting software called MeDoc. Hackers compromised the update mechanism of MeDoc and used it to distribute the NotPetya malware to organizations around the world. The attack caused an estimated $10 billion in damages.
Ticketmaster (2018) – In 2018, Ticketmaster announced that it had suffered a data breach due to a supply chain attack. Hackers compromised the chatbot software of a third-party vendor and used it to steal customer data from Ticketmaster’s website.
ASUS (2019) – In 2019, hackers compromised the software update mechanism of ASUS, a popular computer manufacturer. This allowed them to distribute malware to over a million ASUS customers. The attack was discovered by cybersecurity researchers before any major damage was done.
SolarWinds Supply Chain Attack(2020) The SolarWinds supply chain attack was discovered in December 2020, but its full extent was revealed in 2021. Hackers gained access to the software build system of SolarWinds, a prominent IT management software company, and implanted a backdoor into the software update process. This allowed them to compromise the systems of over 18,000 SolarWinds customers, including many government agencies and large corporations.
Kaseya Supply Chain Attack(2021)- In July 2021, a supply chain attack targeted Kaseya, a software company that provides IT management tools to managed service providers (MSPs). Hackers exploited a vulnerability in Kaseya’s VSA remote monitoring and management software, allowing them to deploy ransomware to over 1,500 organizations.
Microsoft Exchange Server Supply Chain Attack(2021)- In March 2021, Microsoft disclosed that hackers had compromised the software supply chain for its Exchange Server email software. The attack targeted a zero-day vulnerability in the software, allowing the hackers to gain access to the systems of thousands of organizations worldwide.
GitHub (2022) – In April, GitHub’s security team made public a security breach where attackers managed to pilfer OAuth user tokens belonging to third-party integrators, namely Heroku and Travis-CI. These stolen tokens were then exploited to extract data from multiple GitHub customers who had been utilizing OAuth applications provided by these vendors, such as npm and GitHub’s own repository hosting service.
AccessPress (2022) – a well-known developer of WordPress plugins and themes utilized by over thounsands of active websites, fell victim to a breach. The attackers successfully substituted the company’s software with versions that contained backdoors, granting them complete control over websites employing these malicious plugins.
3CX (2023)- The Company’s systems experienced a breach when an employee downloaded a tampered installer for the X_Trader trading software from Trading Technologies onto their personal computer.
The compromised X_Trader application introduced a malware called VeiledSignal, granting the attackers elevated privileges on the employee’s device. With this access, the attackers successfully acquired the employee’s corporate credentials, which enabled them to infiltrate the 3CX systems.
After gaining entry to the 3CX network, the attackers proceeded to collect credentials, expand their reach within the network, and deploy additional malware to compromise both Windows and macOS build environments. Consequently, they were able to distribute malware to 3CX customers.
It is important to note that supply chain attacks are constantly evolving and can occur at any time. It is essential for organizations to remain vigilant and take proactive steps to protect their supply chains against cyber threats.
Assessing the Impact of Supply Chain Cyber Attacks
Supply chain cyber attacks can have significant impacts on businesses, organizations, and individuals.
These attacks can occur in various forms, including malware infections, data breaches, ransomware attacks, and denial-of-service (DoS) attacks, among others.
The impacts of such attacks can be severe and long-lasting, affecting the confidentiality, integrity, and availability of critical business operations and customer data.
Some potential impacts of supply chain cyber attacks include:
1. Financial losses: Supply chain attacks can lead to financial losses in the form of disrupted operations, lost revenue, and remediation costs. For example, a ransomware attack that encrypts critical systems or data can lead to significant downtime, lost productivity, and revenue losses.
2. Damage to reputation: Supply chain attacks can also damage an organization’s reputation, particularly if customer data is compromised. A breach of customer data can result in loss of trust, customer churn, and negative media coverage.
3. Regulatory compliance issues: Organizations may face regulatory compliance issues if they fail to protect customer data adequately. This can result in fines, penalties, and legal liability.
4. Operational disruptions: Supply chain attacks can disrupt critical business operations, resulting in delays, downtime, and reduced productivity. For example, a DoS attack can overwhelm a company’s systems, making it impossible to conduct business.
5. Intellectual property theft: Supply chain attacks can also result in intellectual property theft. Attackers can steal valuable trade secrets, customer data, and other sensitive information, leading to competitive disadvantages.
6. Enabling Hosting of APT or MASS/RASS Malware/Randsomeware as a Service for Customer Environment.
Overall, the impact of supply chain cyber attacks can be significant and long-lasting. It is essential for organizations to take steps to protect their supply chains, including implementing strong cybersecurity measures, regularly reviewing and updating security protocols, and conducting regular security assessments and audits.
Step-by-Step Strategies to Protect Against Supply Chain Cyber Attacks
Protecting against supply chain cyber attacks requires a multifaceted approach that involves various strategies and measures. Here are some step-by-step strategies to help protect against supply chain cyber attacks:
1. Identify potential risks: Identify potential risks and vulnerabilities by conducting regular risk assessments. This will help to identify potential weak links in supply chain and prioritize security efforts.
Risk assessment frameworks are essential tools that organizations use to identify, analyze, and prioritize risks that could affect their operations, assets, or reputation. These frameworks help organizations to establish a structured and systematic approach to risk management by providing a standardized process for evaluating risks and determining the appropriate responses.
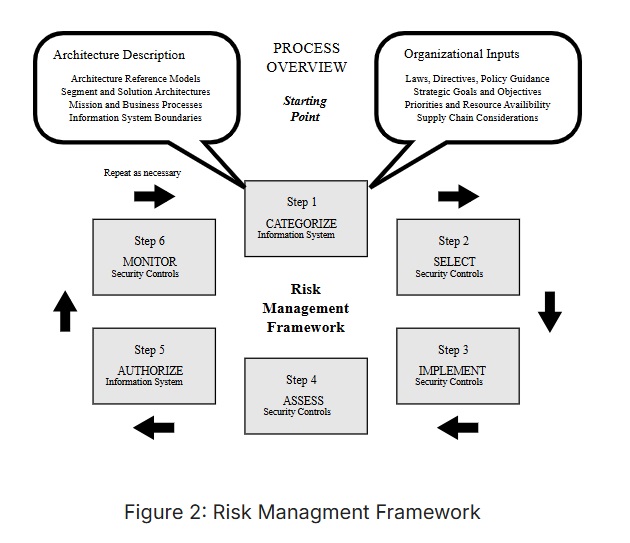
Here are Some of the Most Common Risk Assessment Frameworks:
ISO 31000: This is an international standard that provides guidelines on risk management principles and a framework for risk management that is applicable to all types of organizations. The standard emphasizes the importance of risk identification, analysis, evaluation, treatment, and monitoring.
NIST Cybersecurity Framework: This framework is developed by the National Institute of Standards and Technology (NIST) to help organizations manage and reduce cybersecurity risks. It provides a set of guidelines and best practices for identifying, protecting, detecting, responding, and recovering from cyber incidents.
COSO ERM: The Committee of Sponsoring Organizations of the Treadway Commission (COSO) developed the Enterprise Risk Management (ERM) framework to help organizations identify, assess, and manage risks across the entire organization. The framework emphasizes the importance of aligning risk management with strategic objectives, providing a holistic view of risks, and embedding risk management in the organization’s culture.
FAIR: Factor Analysis of Information Risk (FAIR) is a quantitative risk assessment framework that provides a structured and repeatable approach to risk analysis. The framework uses a taxonomy of risk factors to assess the likelihood and impact of specific risks and to determine the most appropriate risk mitigation strategies.
OCTAVE: Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) is a risk assessment framework developed by Carnegie Mellon University’s Software Engineering Institute. The framework emphasizes the importance of risk assessment tailored to the organization’s specific needs and provides a structured approach to identifying assets, threats, vulnerabilities, and impacts.
Governance, Risk, and Compliance (GRC) : Framework that organizations can use to manage risks and ensure compliance with regulations. In the context of supply chain attacks, GRC can be used to identify potential risks in the supply chain and implement controls to reduce those risks. Here are some ways that organizations can use GRC to reduce risk in supply chain attacks:
1. Verify the security posture of your partners and vendors: Verify the security posture of your suppliers, partners, and vendors by conducting regular security assessments and audits. This will help you ensure that they have adequate security policy and control as Zero Trust Policy measures in place to protect your data and systems.
2. Implement access controls: Implement access controls to limit access to your systems and data. This includes using privilege access management, multi-factor authentication and role-based access controls.
3. Monitor your systems: Monitor your systems and networks for suspicious activity and potential threats. This includes using SIEM,SOAR,IPS systems, monitoring logs, and conducting regular vulnerability assessments.
4. Train your employees: Train your employees on cybersecurity best practices, such as how to identify and report suspicious activity, how to create strong passwords, and how to avoid phishing and social engineering attacks.
5. Plan for incident response: Develop an incident response plan that outlines the steps to take in the event of a supply chain cyber attack. This includes identifying the key stakeholders, assessing the impact of the attack, containing the attack, and recovering from the attack.
By following these strategies, organizations can help protect sensitive data within the supply chain and minimize the risk of data breaches and other security incidents.




