What is Zero Trust Network Access (ZTNA)?
Zero Trust, as a cybersecurity paradigm, is characterized by a fundamental shift in the traditional security mindset. It departs from the conventional assumption that all entities residing within the secure confines of a corporate firewall are inherently trustworthy. Instead, the Zero Trust model operates on the premise that unauthorized breaches may occur at any point within the network infrastructure.
The central concept of Zero Trust can be encapsulated in the succinct axiom: “Never trust, Always verify”
This principle underscores the imperative of subjecting every access request, irrespective of its origin or target resource, to a comprehensive and systematic authentication, authorization, and encryption procedure before granting access privileges.
Principles of Zero Trust Network Access Essential in a Perimeterless World?
Zero Trust is a cybersecurity model that emphasizes strict identity verification and continuous monitoring of network access, regardless of whether it originates from inside or outside the network perimeter.
This approach assumes that threats can exist both inside and outside the traditional network boundaries, making it essential to trust nothing and verify everything.
The Zero Trust model is built on fundamental principles:
1. Verify Identity: The cornerstone of Zero Trust is to authenticate and verify the identity of all users and devices attempting to access the network or resources. This involves strong, multi-factor authentication (MFA) methods to ensure that only authorized entities gain access.
2. Least Privilege Access: Limit access permissions based on the principle of least privilege. Users and devices should only have access to the specific resources and data required for their roles or tasks. This minimizes the potential for lateral movement by attackers.
3. Micro-Segmentation: Divide the network into smaller, isolated segments, or micro-segments, with strict access controls. Each segment should have its own access policies, creating barriers that prevent unauthorized lateral movement. This limits the potential blast radius of security breaches.
4. Continuous Monitoring: Implement continuous monitoring and analysis of network traffic, user behavior, and device activity. By constantly assessing for anomalies and unusual activities, organizations can quickly detect and respond to potential threats, reducing the dwell time of attackers.
5. Security Analytics: Employ advanced security analytics and machine learning to identify unusual patterns or behaviors that may indicate security threats. These analytics can help organizations proactively detect and mitigate threats before they escalate.
6. Secure Access Everywhere: Extend Zero Trust principles beyond the traditional network perimeter. With the increasing adoption of cloud services and remote work, security should be applied to any device, user, or network location, ensuring secure access from anywhere.
7. Data-Centric Security: Focus on protecting the data itself rather than solely relying on perimeter defenses. Implement encryption, data classification, and data loss prevention (DLP) measures to safeguard sensitive information, even if network boundaries are breached.
By following these seven principles, organizations can create a more robust and adaptive security posture that is better equipped to defend against modern cyber threats.
The Zero Trust model helps organizations shift from a perimeter-centric approach to a more dynamic and responsive security framework that is better suited to the evolving threat landscape.
ZTNA Versions 1.0 & Version 2.0
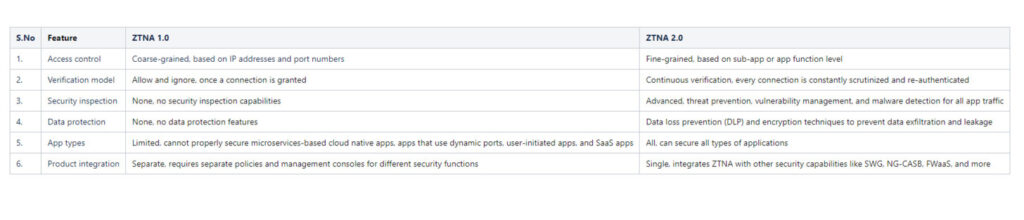
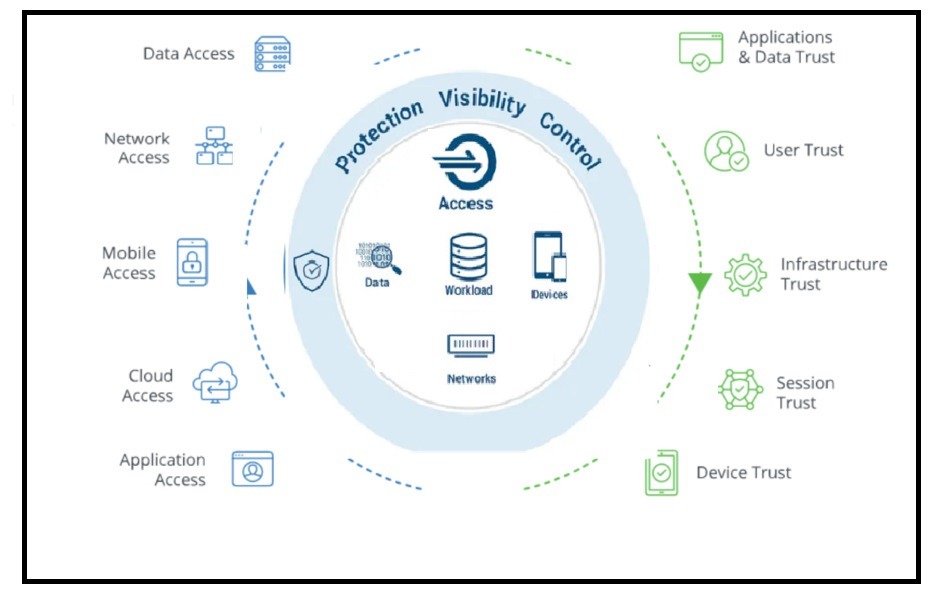
Zero Trust Network Access (ZTNA) is a security framework that focuses on authenticating and authorizing users and devices before granting them access to network resources. ZTNA offers a range of use cases that enhance security and control.
Here are five specific ZTNA use cases:
1. Data Security: ZTNA plays a crucial role in protecting sensitive data. It ensures that only authorized users and devices can access data resources, reducing the risk of data breaches. By verifying user identities and enforcing access policies, ZTNA helps organizations maintain data confidentiality and integrity.
2. Device Posture/Profile Management: ZTNA incorporates device posture assessment, which evaluates the security health of devices attempting to access the network. It checks factors like device security patches, antivirus software, and configuration compliance. Devices that meet predefined security criteria are granted access, while those that don’t are either denied access or given restricted access until they meet the requirements. This ensures that only secure devices can connect to the network, reducing the risk of compromised endpoints.
3. Inspection: ZTNA enables inspection of traffic even after users and devices have been authenticated. It allows organizations to monitor and analyze network traffic for threats and anomalies. This is crucial for identifying and mitigating security incidents, ensuring that malicious activity is detected and blocked promptly.
4. IoT and OT : Internet of Things (IoT) and Operational Technology (OT) devices are often challenging to secure. ZTNA helps address this by controlling access to these devices. It ensures that only authorized users and applications can communicate with IoT and OT devices, reducing the attack surface and protecting critical infrastructure.
5. Data Center & Cloud: ZTNA is highly valuable in data center and cloud environments. It provides secure access to critical resources hosted in data centers or the cloud. Users and devices are required to authenticate and follow strict access policies, reducing the risk of unauthorized access, data breaches, and lateral movement within these environments.
ZTNA is instrumental in securing access to cloud-based services and applications e.g CASB. It ensures that users are authenticated and authorized to access cloud resources, whether they are hosted on public cloud platforms like Public & Private cloud environments.
The Benefits of ZTNA
A key advantage of ZTNA is that it can be deployed without making major changes to the existing network infrastructure. ZTNA solutions work by intercepting traffic at the edge of the network and then authenticating and authorizing the user or device before allowing access to the requested resources.
This approach has a number of benefits.
Here are ZTNA Approach Benefit’s:
1. Streamline Remote Access Management : ZTNA’s architecture outperforms legacy technologies like Virtual Private Networks (VPNs) in terms of remote access management and security policy enforcement. The architecture ensures a consistent and simplified approach to these critical functions.
2. Comprehensive Data and Application Protection : ZTNA’s architecture extends robust security controls to safeguard sensitive data and applications. Whether they reside on-premises or in cloud environments, whether in transit or at rest, these security measures encompass diverse aspects such as encryption, authentication, health/posture/compliance assessments.
3. Mitigate Insider Threats : Departing from the conventional paradigm of affording implicit trust to entities within the network perimeter, ZTNA’s architecture proactively addresses insider threats. Default trust is rescinded, significantly curtailing the potential for malicious activities.
4. Precision Access Policies and Lateral Movement Restriction: The architecture bolsters cybersecurity by enforcing granular access policies that operate at a resource-specific level. This approach constrains lateral movement within the network, substantially reducing the susceptibility to breaches.
5. Swift Breach Management and Recovery: In the event of a breach, ZTNA’s architecture augments incident response capabilities. It facilitates the timely detection, responsive actions, and efficient recovery procedures, effectively mitigating the impact of breaches with Key Performance Indicator (KPI) e.g MTTD_Detect, MTTD_Dwell, MTTR_Respond ,MTTR_Recover.
6. Enhanced Visibility and Risk Assessment: The architecture augments operational visibility by capturing detailed insights into user and entity activities. Comprehensive monitoring and logging of sessions and actions enable comprehensive understanding of the what, when, how, and where of these activities. Real-time risk assessment is enabled through exhaustive authentication logs, assessments of device and resource health, and analysis of user and entity behavior
7. Improved compliance: With ZTNA, you can granularly control access to your data and applications. This means that you can easily meet even the most stringent compliance requirements.
Challenges of Implementing ZTNA
Implementing Zero Trust Network Access (ZTNA) can offer significant security benefits, but it also comes with its fair share of challenges and complexities.
Here are some of the key challenges organizations may encounter when implementing ZTNA:
1. Legacy Infrastructure : Many organizations have legacy network infrastructure and applications that were not designed with ZTNA principles in mind. Adapting or transitioning these systems to work within a ZTNA framework can be challenging and may require significant effort and investment.
2. User Experience & Education : Stricter access controls and continuous verification can potentially lead to a more complex user experience. Employees may face additional authentication steps or encounter delays in accessing resources, which can impact productivity and user satisfaction if not carefully managed.users need to be educated and trained on the new security protocols and practices to ensure they understand their role in maintaining security.
3. Resource Discovery : Accurately identifying and classifying all network resources, including applications, devices, and data, is crucial for effective ZTNA implementation. However, this can be a complex task, especially in large and dynamic environments.
4. Latency & Integration Complexity : Integrating ZTNA solutions with existing security tools, identity management systems, and network infrastructure can be challenging. Ensuring seamless interoperability and maintaining a holistic security posture requires careful planning and testing.
5. Scalability : Scaling ZTNA to accommodate a growing user base or an expanding network can be complex. Organizations need to design their ZTNA architecture with scalability in mind to avoid bottlenecks and performance issues.
6. Costs : ZTNA implementation can involve significant upfront costs, including the acquisition of new security technologies and the reconfiguration of existing infrastructure. Organizations must carefully consider their budget constraints and allocate resources appropriately.
7. Management and Monitoring : ZTNA requires continuous monitoring and management of user access and network activity. Organizations need the right tools and skilled personnel to oversee and respond to security incidents effectively.
8. Vendor Selection : ZTNA solution and vendors can be challenging. Organizations need to evaluate various options, consider their specific needs, and select vendors that offer robust and reliable solutions.
9. Zero Trust Culture : Implementing ZTNA is not just a technological change but also a cultural shift. Building a Zero Trust culture within the organization, where trust is never assumed and security is everyone’s responsibility, can be a long-term challenge.
While ZTNA offers enhanced security and adaptability, organizations need to address these challenges systematically to ensure a successful implementation and maximize the benefits of a Zero Trust approach to network security.
Final Thoughts on Zero Trust Network Access and Cybersecurity
Zero Trust Network Access (ZTNA) is not merely a cybersecurity trend but a transformative paradigm that is increasingly essential in an ever-evolving threat landscape.
Cyber Attack Phases’ are have different Tatic, Technique and Procedure (TTP) for Cyber attacks.
To minimize attack surface and The goal of ZTNA is to make it more difficult for attackers to gain a foothold in the network.
ZTNA creates multiple layers of security that can make it much harder for an attacker to move laterally through the network. In wrapping up our blog on ZTNA and its significance in the realm of cybersecurity,
it’s important to reiterate a few key takeaways:
1. Security Beyond Perimeters :ZTNA challenges the traditional perimeter-centric security model, recognizing that threats can emerge from both external and internal sources. This shift signifies a more holistic and proactive approach to safeguarding digital assets.
2. Continuous Authentication : ZTNA’s core tenet of “never trust, always verify” underscores the importance of ongoing authentication and authorization. This dynamic verification ensures that access privileges remain valid throughout a user’s session, reducing the attack surface.
3. Adaptability and Flexibility : ZTNA is inherently adaptable, making it well-suited for contemporary work environments characterized by remote work, cloud services, and mobile access. It enables organizations to secure their resources regardless of users’ locations or devices.
4. Granular Access Control : The implementation of least-privilege access and microsegmentation empowers organizations to finely control who can access specific resources. This principle minimizes lateral movement and limits the potential impact of security breaches.
5. Balancing Security and User Experience : While ZTNA bolsters security, organizations must strive for a balance that preserves user experience and productivity. Ensuring that legitimate users can access resources efficiently is crucial.
6. Data-Centric Approach : ZTNA aligns with a data-centric security strategy, emphasizing the protection of data assets themselves. This focus is crucial as data breaches continue to pose substantial risks.
7. Security Posture Enhancement : Implementing ZTNA provides an opportunity for organizations to assess and enhance their overall security posture. It encourages a proactive approach to improving security practices, awareness, and infrastructure.
8. Challenges and Investments : Organizations should anticipate challenges such as integration complexities, the need for user education, and initial investment requirements. Addressing these challenges systematically is essential for a successful ZTNA implementation.
9. Regulatory Compliance : ZTNA can be a valuable ally in meeting regulatory compliance requirements by providing a robust framework for access control, data protection, and real-time monitoring.
Conclusion : Zero Trust Network Access is a forward-thinking approach to cybersecurity that offers enhanced protection and adaptability in an era of persistent cyber threats.
As the cyber landscape continues to evolve, embracing the principles of ZTNA is a proactive step toward building a resilient and future-ready security posture. Organizations that prioritize ZTNA are better positioned to safeguard their digital assets and maintain operational continuity in the face of evolving security challenges.




